
Data security
How to protect your data?

Dozenten: Rainer R. | Tobias R.
06.10.2016
Let’s have a party!
- Introduction
(Tobias) - Digital Self Defence matters
(Tobias) - Limits of Digital Self Defence, Attack Vectors, Thread Models
(Rainer) - Passwords, Passphrases and Password Managers (Tobias)
- Harddrive-/File Container Encryption
(Rainer) - Avoiding Digital Traces
(Tobias, Rainer)
Let’s start a party!


Privacy Leipzig (Bündnis Privatsphäre Leipzig e. V.) is a citizens' initiative focused on and against mass surveillance in the context of a democratic and a constitutional state based on justice and integrity (Rechtsstaat) with the goal to start a public debate and boost a discourse about this topics and its relationships

About us
- constituted as a local protest group (grassroots movement) in the wake of the Snowden revelation in 2013
- more formalised as a citizens' initiative in the same year
- constituted as a registered society in 2014 and recognized as a charitable organization in 2015

How we work
- regular meetings in Sublab and at Autodidactic Initiative (ADI)
- focused on regional actions and awareness rising
- regional cooperations with other groups and institutions (Sublab, ADI, Medienstadt Leipzig e. V., Mitteldeutsches Internetforum, University of Leipzig, Volkshochschule)
- federal cooperations with groups in Berlin and Cologne (#StopWatchingUs Köln, #wastun gegen Überwachung Berlin)

Our Topics
I
- digital revolution in general
- no difference between digital rights and human rights
- data protection and digital self-defence
- digital revolution and economy: surveillance capitalism
- privacy vs. publicity (post-privacy?) as mode of being in the world

Our Topics
II
- mass surveillance of secret services
- Telecommunications data retention (Vorratsdatenspeicherung)
- CryptoWars and digital self-defence
- SmartCities, Internet of Things

Projects: CryptoParties
CryptoParty is a decentralized, global initiative to introduce the most basic cryptography programs and the fundamental concepts of their operation to the general public.
We understand Cyptoparties as an opportunity to provide knowledge and experience for “digital self-defence” against mass surveillance.

CryptoParty 2/2016, 1/2017
- 12. Oktober 2016 – File and Disk Encryption
- 09. November 2016 – Alternative Soziale Networks and Cloud-Systeme
- Dezember 2016 – Privacy and Security with Windows 10, use of virtual machines, QubesOS, Whonix
- 11. January 2017 – Web tracking and anonymous communication (VPN, Tor, Tails)
- 08. February 2017 – E-Mail encryption with GnuPG (PGP), passwords
- 08. March 2017 – Messenger & Chats
Digital Self Defennce
Need of Digital Self Defence?
- How to exercise privacy as a principle human right in the digital age
- Self Defence against mass surveillance, data retention, tracking and BigData (surveillance capitalism)
digital self defence
mass surveillance by example

digital self defence
tracking (examples)
- Google compiles profiles of us from Google searches, e-mails, tracking analysis ... for personalized advertising
- Facebook by mapping relationships and networks
- amazon by tracking buying patterns and preference or even the reading behaviour (Kindle)
digital self defence
Big Data Analysis
- BigData is used to create profiles and analysis based of large collection of data
- BigData as a business model
- Public-Private-Partnership
Digital Self Defence
Digital Revolution?
- surveillance as a technique of power and the risk of manipulation
- Digital revolution als transculturation → change of human behaviour
- What kind of society/social system we are dealing with here? (Panoptikum, Banoptikum, Synoptikum)
CryptoWars 2.0/3.0
Encryption under attack
scope of action
scopes of actions according Bruce Schneier (Data vs Goliath)
- avoid surveillance
- block surveillance
- tamper surveillance
- sabotage surveillance (mostly not legal!)
Limits of Digital Self Defence
Encryption works. Properly implemented strong crypto systems are one of the few things that you can rely on.
Went wrong
Examples of Security breaches
Get a feeling
analysing risks with thread models
thread models:
- describe vectors of attack, show behaviours, or ways and forms of data transmission, that could bear risks
- allow to balance the use of technical solutions like end to end encryption or transport encryption
- helps to define ones own level of security precautions and to find the right dealing with it
The Questions
interest of protection and protection framework
- What do I need to protect?
- How likely it the necessity to protect?
- Against whom do I need to protect?
- What are the consequences if the protection fails?
- How much effort do I want or need to put into the protection?
- What I am willing to bear to protect?
Assets
examples
- passwords
- money
- data (private photos, videos, documents, etc.)
- chats, conversations, correspondences
- metadata
- private oder business secrets
Attacker
examples
- security agencys (NSA, GCHQ, BND)
- (nosy) colleagues, neighbours, parents, classmates and so on
- (nosy) security or police forces
- thefts, cyber criminals
- businesses how use data for profiling to sell adds
Consequences of failing Protection
examples
- identity-theft
- loosing autonomy:
- advertising businesses collecting and analysing my data
- provider filtering or reading tweets, facebook-posts, e-books etc.
- takeover of devices: smartphone, laptop, tablet, e-book-reader
- loss of data: apps that spread data or do not securely transmit them, blackmail-trojaner encrypting data or OS
attack vectors
examples
- physical access family member installs monitoring or surveillance software
- interception of data transmission attacker intercept LAN/WLAN traffic (man in the middle)
- phishing/trojaner, manipulation of the endpoint of communication attacker uses fake websites
- manipulation of the OS/of programs attackers uses bugs in OS or applications
Conclusion
thread models as a way to empowerment
- thread models help to balance risks for data security and data protection
- thread models identify assets to protect, adversaries, risks and attack vectors
- threads can better be judged and more meaningful decided if and which action to take
pushing the boundaries
rules and steps
- update, updates, updates
- backups, backups, backups
- anti virus software (+/-)
- encryption/disguise
- unplugged system: Sensible Daten auf System ohne Netzzugang aufbewahren und verschlüsseln
Limits

Limits of Harddrive-/File Container Encryption
- data protection and security only if not mounted
- use OSS implementations, for commercial vendors could be forced to include backdoors
- only use well known and documented algorithms
- use products under active development (patches/bug fixes for security holes, new features if demanded by technical progress)
- availability for OS
Passwords, Passphrases and Password Managers
- Password Strategies
- Password Manages
LOL, owned
Security Breaches and Passwords
LOL, owned
Security Breaches and Passwords

Do not
Sony

Sony Kept Thousands of Passwords in a Folder Named "Password"
Do not
Bad Passwords
- short passwords
password1235,secret- number sequences:
12345 - names, literary character, venues/places, fictional venues places etc. (dictionary attack)
- Date of birth, anniversaries
- Add sequences to a given password:
password1,password2,password3etc. - A single password for everything
The secret of a strong password
- use of all possible letters
- different password for each purpose
- lenght beats complexity
- use case defines strategy
- mnemonics
- leetspeak? (
1337 5P34K)
Strategy I
Don't forget!
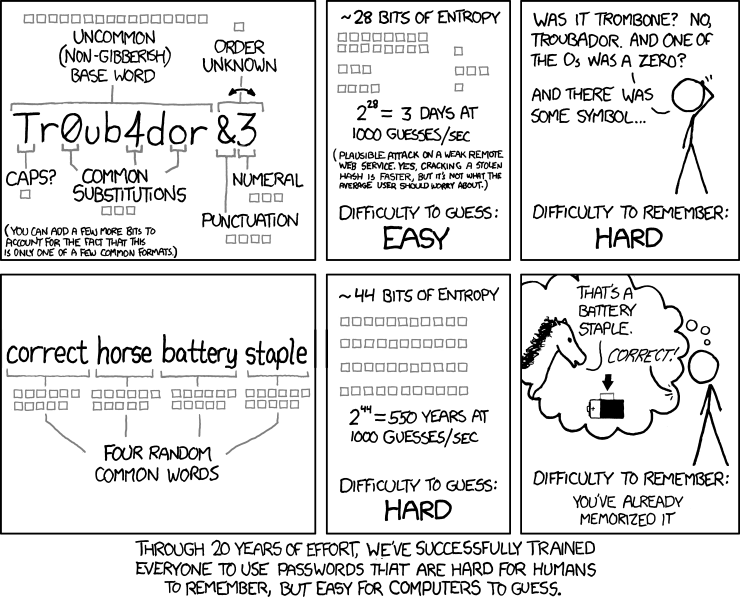
Strategie I
Don't forget!
- memorable long phrase or word combinations
- lenght beats complexity
- Mnemonics
- imagination, association, location
- repetition: Every day usage!
- recommend for master passwords, full disk encryption passwords, root passwords
Strategie II
Generate
- Use of an password generators (OpenSource)
- Don used a cloud based tool
- lenght outperforms complexity
- recommended for your thousands of web service accounts
Strategie III
Diceware™
- based on an idea of Arnold G. Reinhold
- simple choose words from a dictionary word list by rolling a dice (Diceware Word List)
- password-combination must provide at least 64 bit entropy to last a year
- 80 bits correlates up to 8 words and is considered as a good password
- 120 bits correlates up to 12 words and is considered as a strong password
Strategie III
Diceware™ - Software Tools
- Windows: Dice Ware Password Generator
- Linux: rusty-diceware, secpwgen
- Android: Diceware (only 6 words)
only use Software build on top of cryptographically secure pseudorandom number generator
Harddrive-/File Container Encryption
What for?
- encryption of multiple files (for example whole directories or directory trees)
- offers protection for all stored data against (offline-)theft (especially important for mobile devices like notebooks) but also against nosy stranger or fiends
- protect against data recovery after sale, on repair or after dispose of data medium
Harddrive-/File Container Encryption
- two possibilities
- partitions or whole harddisks/SSDs
- file container, stored like normal files on the data medium (therefore easy use for backup)
- if mountet both are to use like normal drives, transparent to the system
- if unmounted no access to the data possible and no information about the stored data are revealed
TrueCrypt
informations about the program: https://en.wikipedia.org/wiki/TrueCrypt
- problem: no more actively developed
- bugs will not be fixed (examples CVE-2015-7358 and CVE-2015-7359)
- no new features (UEFI/GPT support missing)
- Very special licence so future development is difficult
- originale website closed, only copies available
TrueCrypt
- but: one of the best audited OSS-Projects
- audit for the latest full functional version (7.1a) without security bugs in the crypto part of teh implementation
- very good documentation
- open source
- for different OSs (Windows, Mac, Linux)
TrueCrypt
- features:
- encryption of the OS (windows only) (entire storage device)
- partitions
- file container
- plausible deniability
- Alternatives? VeraCrypt (TrueCrypt-fork under active development)
TrueCrypt or VeraCrypt?
TrueCrypt download: https://github.com/AuditProject/truecrypt-verified-mirror
VeraCrypt download: https://veracrypt.codeplex.com/releases/view/616110
- sources for TrueCrypt: verified by the Open Crypto Audit Project, they also did the cryptoaudit for TrueCrypt
- sources for VeraCrypt: from the project pages
- both portabel useable, but administration rights necessary (Windows)
TrueCrypt/VeraCrypt
How does it work? (1)
- masterkeys and additional information for de- and encryption of the content of containers, partitions or drives will be encrypted stored in the volume header
- for there encryption a header key will be derived from the password or/and keyfile(s) with PBKDF2 (Password-Based Key Derivation Function 2)
- VeraCrypt additional: PIM (Personal Iterations Multiplier)
TrueCrypt/VeraCrypt
How does it work? (2)
- mode of operation is XTS the widespread standard for data medium encryption used in BestCrypt, dm-crypt, FreeOTFE, DiskCryptor, FreeBSD geli, OpenBSD softraid disk encryption software and Mac OS X Lion FileVault 2
TrueCrypt/VeraCrypt
algorithms of encryption (1)
- all algorithm were finalists for the Advanced Encryption Standard (AES) for the National Institute of Standards and Technology (NIST) in the USA in 2000
- Rijndael/AES (Joan Daemen, Vincent Rijmen), the winner of the contest
- Serpent (Ross Anderson, Eli Biham, Lars Knudsen)
- Towfish (Bruce Schneier, Niels Ferguson, John Kelsey, Doug Whiting, David Wagner und Chris Hall)
- cascading possible → higher security but more time for de- and encryption needed
VeraCrypt only
algorithms of encryption (2)
- Camellia, developed by Mitsubishi Electric and NTT of Japan, approved by the European Union's NESSIE project and the Japanese CRYPTREC project.
- Magma (GOST89), in a modified version, a national standard of the Russian Federation
- Kuznyechik, a national standard of the Russian Federation
TrueCrypt/VeraCrypt
Hash-Algorithmen
- RIPEMD 160, is a strengthened version of the RIPEMD hash algorithm that was developed in the framework of the European Union's project RIPE
- SHA-512(also SHA-256 in VeraCrypt), hash algorithm designed by the NSA and published by NIST
- Wirlpool, selected by the NESSIE-project (New European Schemes for Signatures, Integrity and Encryption) and adopted by ISO
- Streebog-512 (VeraCrypt only) Russian national standard GOST R 34.11-2012 Information Technology - Cryptographic Information Security - Hash Function, also described in RFC 6986
Alternatives
Windows
- Bitlocker, by Microsoft, from Windows Vista, often only in Pro-Versions useful, closed source. Bitlocker was weakend by Microsoft as they removed the Elephant Diffuser algorithm.
- in Windows 10 the recovery keys by default will be stored in the Microsoft Cloud (background an workaround)
Alternatives
Mac OS X/Linux/BSD
- Lion’s FileVault 2 Mac OS X, closed source
- dm-crypt with LUKS, via repository from the distribution
- tcplay, TrueCrypt compatible, command line tool for Dragonfly BSD and Linux
infos and download: https://github.com/bwalex/tc-play
Avoding digital traces

- useful as live-system or in persistant-mode (from USB-stick with encrypted partition for user data)
- bootable from DVD or USB-stick
- based on Debian Linux
- nearly all programs for digital life and work included
- no traces on the machine where you use it
- as live system useful at different machines
- bonus: uses the TOR-network for internet access

How to
- download
- check GPG-signatur and/or hashsum download program for Windows to calculate hashsums
- burn to DVD (Live-system)
- to use the persistant-mode install to USB-stick/SD-card from running TAILS
Hint: not every machine can boot all media!

Thank you!
